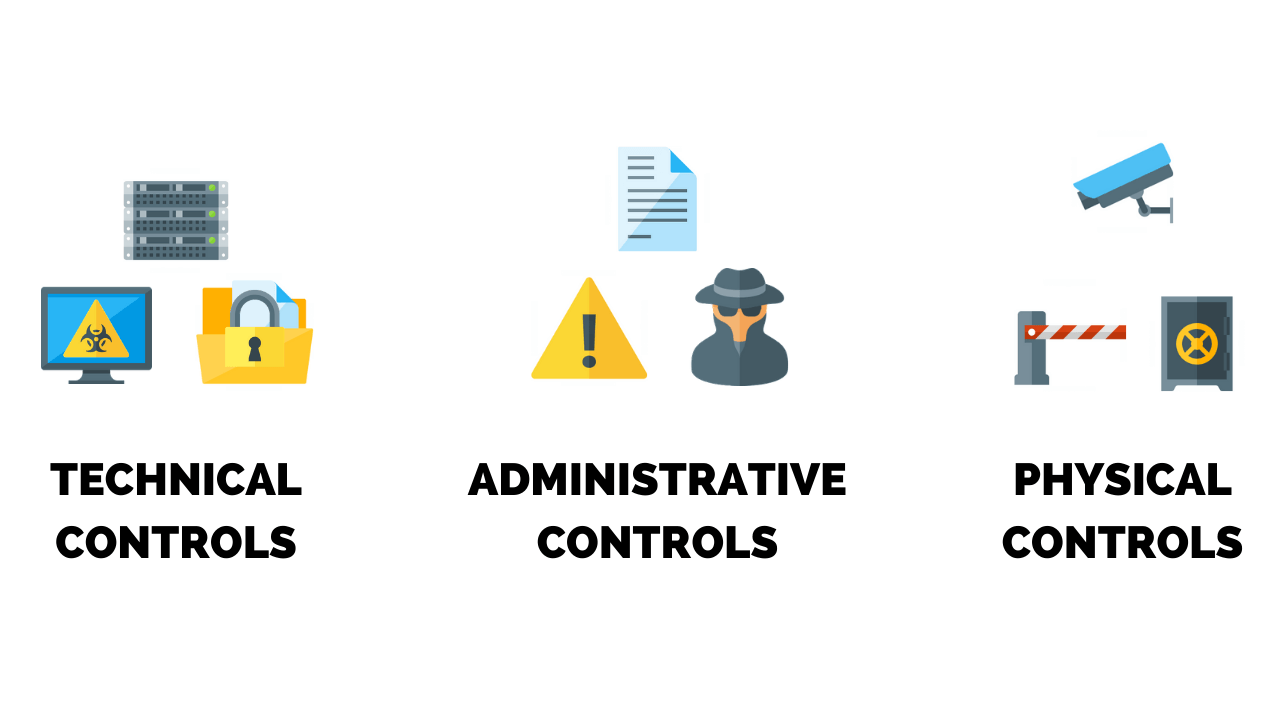
What Guidance Identifies Information Security Controls - Organizations have flexibility in applying the. The document explains the importance of protecting the confidentiality of pii in the context of information security and. This combined guidance is known as the dod information security program. Security and privacy controls for federal information systems and organizations. The eo focused on setting and establishing clear security requirements (applying multifactor authentication, encrypting data at. The updated security assessment guideline incorporates best practices in information security from the united states.
Organizations have flexibility in applying the. The document explains the importance of protecting the confidentiality of pii in the context of information security and. The eo focused on setting and establishing clear security requirements (applying multifactor authentication, encrypting data at. The updated security assessment guideline incorporates best practices in information security from the united states. Security and privacy controls for federal information systems and organizations. This combined guidance is known as the dod information security program.